The 2.8.0 release passed testing earlier this month and is available for production usage by clients.
In a break from previous release post formats, we're going to focus on key functionality across multiple image led posts, to give a better understanding of what's new. First up is the move to supporting integration with multiple Microsoft Azure Active Directories.
What is Microsoft Azure Active Directory?
Microsoft Azure Active Directory (now rebranded as Microsoft Entra ID) is a cloud-based identity and access management system. At a high level it is a list of an organisation's staff, and it can be integrated with other systems so that Active Directory handles the authentication process. For example, when you log in to Windows on a work computer, you're most likely authenticating against Active Directory.
This is beneficial as it means there is a single definitive source for valid user accounts in your organisation, removing the administrative headache of maintaining user lists in individual systems. Microsoft Azure Active Directory is very common as it is a core part of enterprise Microsoft setups, so any organisation using a Microsoft product such as Windows, Office 365, Teams etc is likely to be using it.
Public Platform has two optional pieces of functionality within it that work with Active Directory:
- Single Sign On
- Staff Directory
What is Single-Sign On (SSO)?
"Single Sign On" means logging in once on a central system and then being able to access other systems without having to log in again. With Public Platform it is possible to configure your site to offer authentication against a Microsoft Azure Active Directory instance. This means users log in once using their normal Windows account credentials and can then log in to your Public Platform site without having to enter a username or password again. This process is show in the screenshots below:
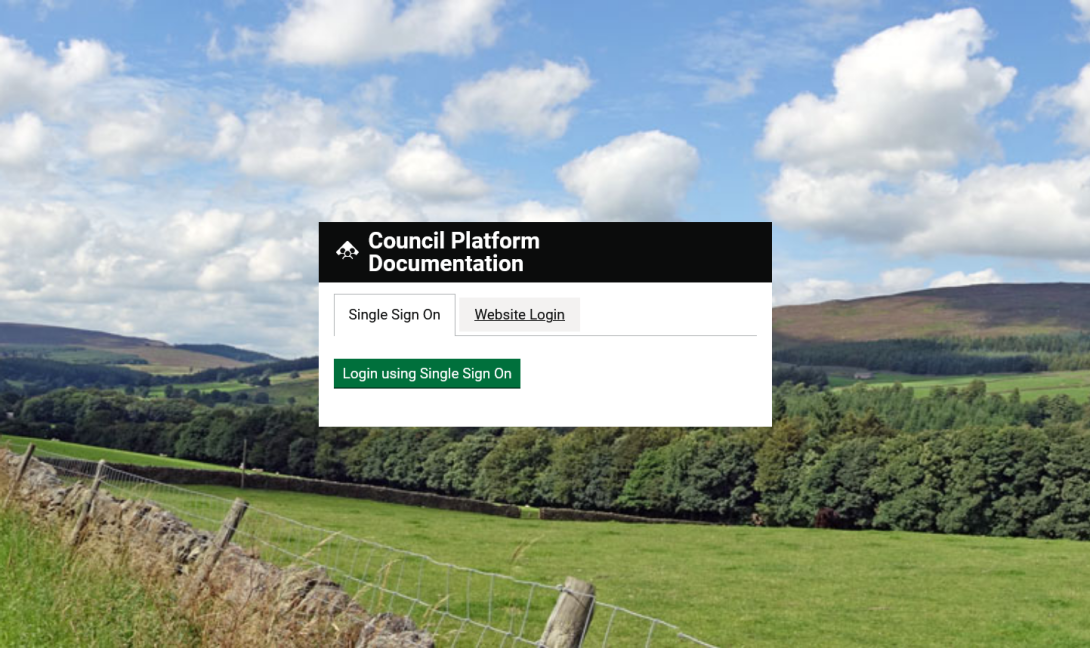
The Single Sign On login form is very simple!
Note, it's possible to retain a manual login option (shown here as the "Website Login" tab) for users who don't have an Active Directory account.
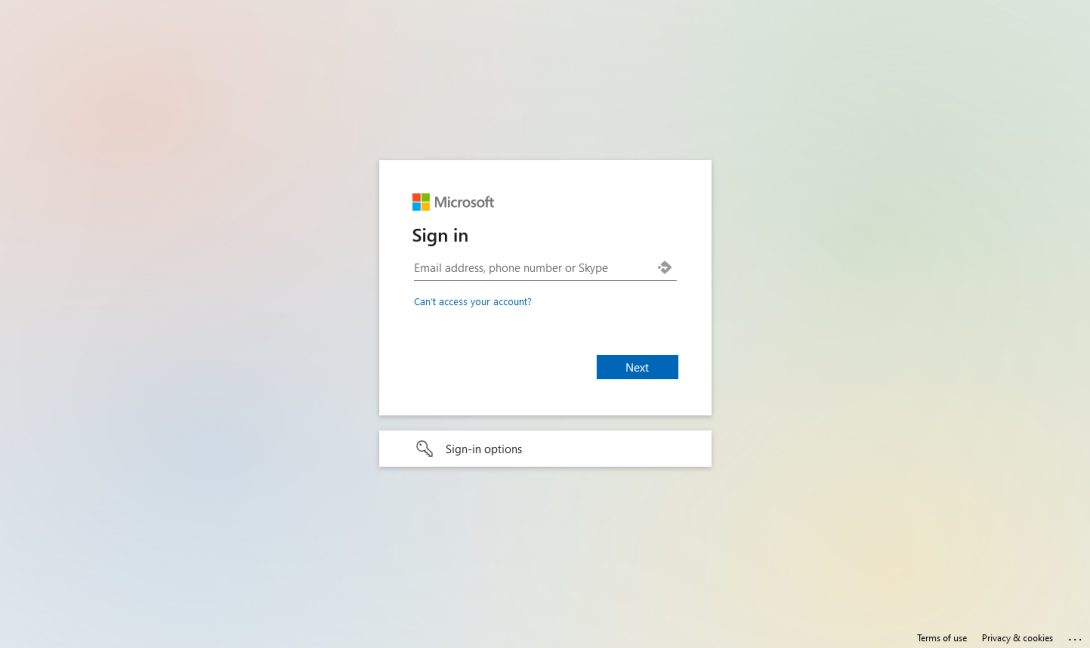
Upon clicking the "Login using Single Sign On" button, you're redirected to a Microsoft Azure Active Directory login page.
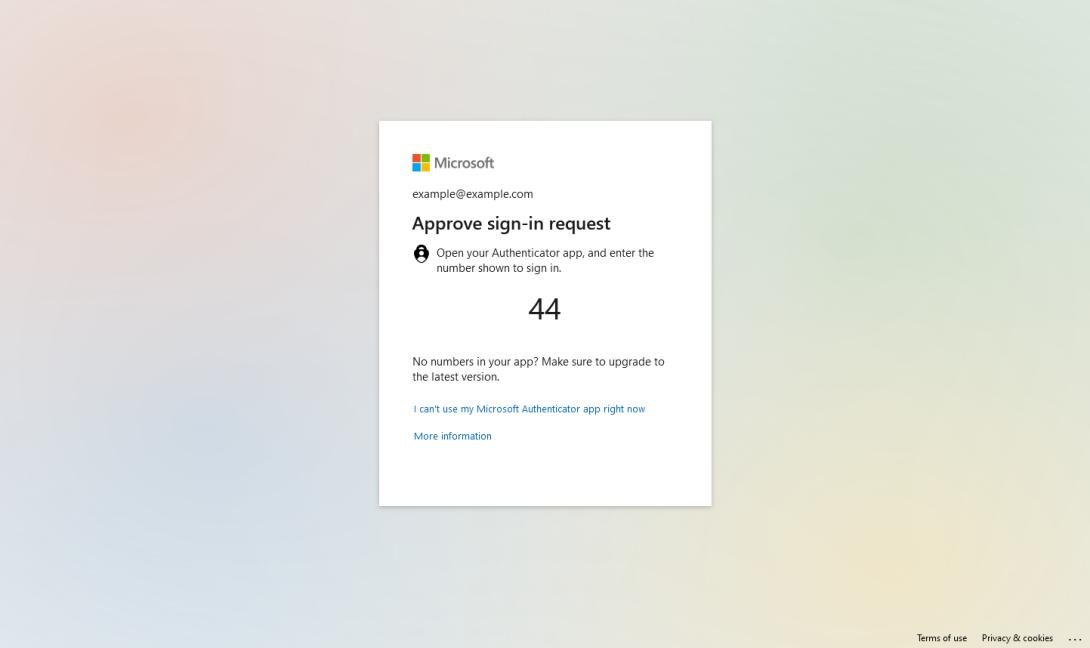
Depending on your Active Directory configuration, you will be prompted to enter a password and/or confirm your login using the Microsoft Authenticator app.
SSO is better for security as your organisation's IT team define security policies centrally for Active Directory (e.g. password policy, two-factor authentication policies, automated logout settings, valid networks for logging in etc) and can also block user accounts or reset passwords immediately.
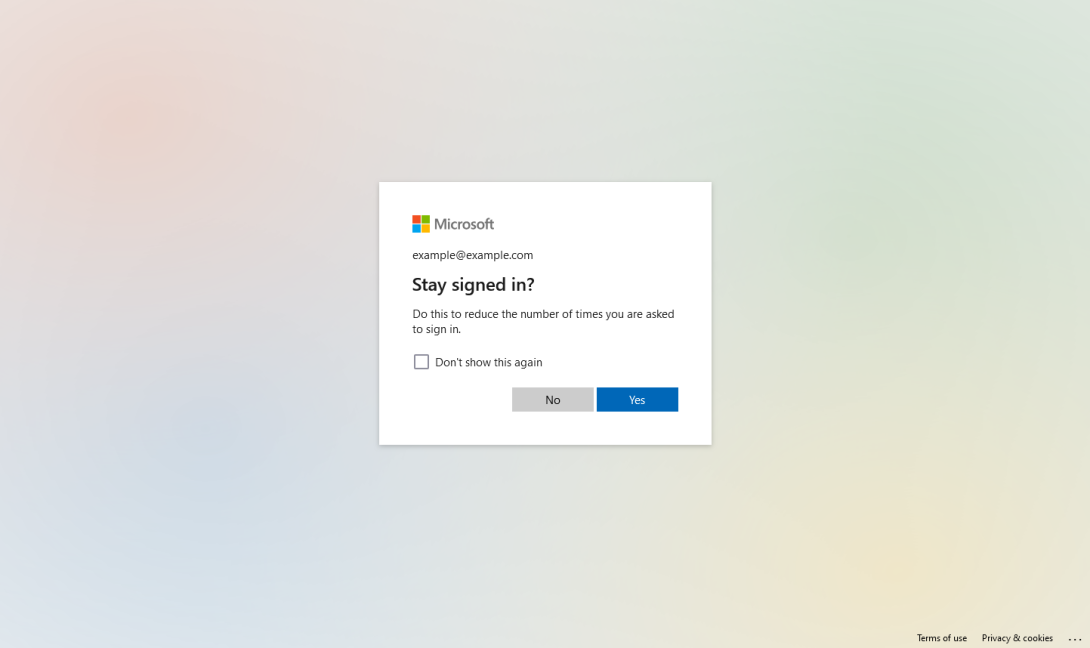
Once you've authenticated, you can opt to stay signed in so you won't be prompted to log in again unless your user session times out, or you switch a computer.
When authentication is complete, you are redirected back to the Public Platform site.
Your user account on the Public Platform site is populated with data from Active Directory. If the details on Active Directory change (e.g. name changes) then the account details on Public Platform will automatically be updated.
Accounts that are deactivated or deleted in Active Directory automatically become blocked in Public Platform.
SSO can be configured so that anyone with an active account on Active Directory can log in to a Public Platform site, without any manual intervention. On the first login, the Public Platform account is created automatically, pulling all data from Active Directory. This makes SSO a "must have" for sites with large number of authenticated users, as manually curating accounts is not feasible.
Moving to multiple Active Directory instances
Brentwood and Rochford Councils now share a single intranet site powered by Public Platform. As they both have Active Directory and very large userbases, it makes sense to use SSO for controlling access to the site. Previously, SSO assumed only one Microsoft Azure Active Directory instance as an authentication source. We've extended the functionality to track multiple Active Directory instances, so users from separate organisations can now log in to the same Public Platform site using SSO. This includes the syncing of accounts so that when an account is deleted from an AD instance, it is blocked on the Public Platform site.

Two Active Directory instances, two buttons - simple!
Under the hood, things are a bit more complicated than that!
Staff Directory functionality
Public Platform sites have the ability to create staff directories, with data being sourced from Active Directory, manual content edits, or a hybrid of the two.
As with SSO, we've extended the Staff Directory functionality to work with multiple Active Directory instances. So Staff Directory entries are created, updated and deleted automatically as the source Active Directory instances are updated.
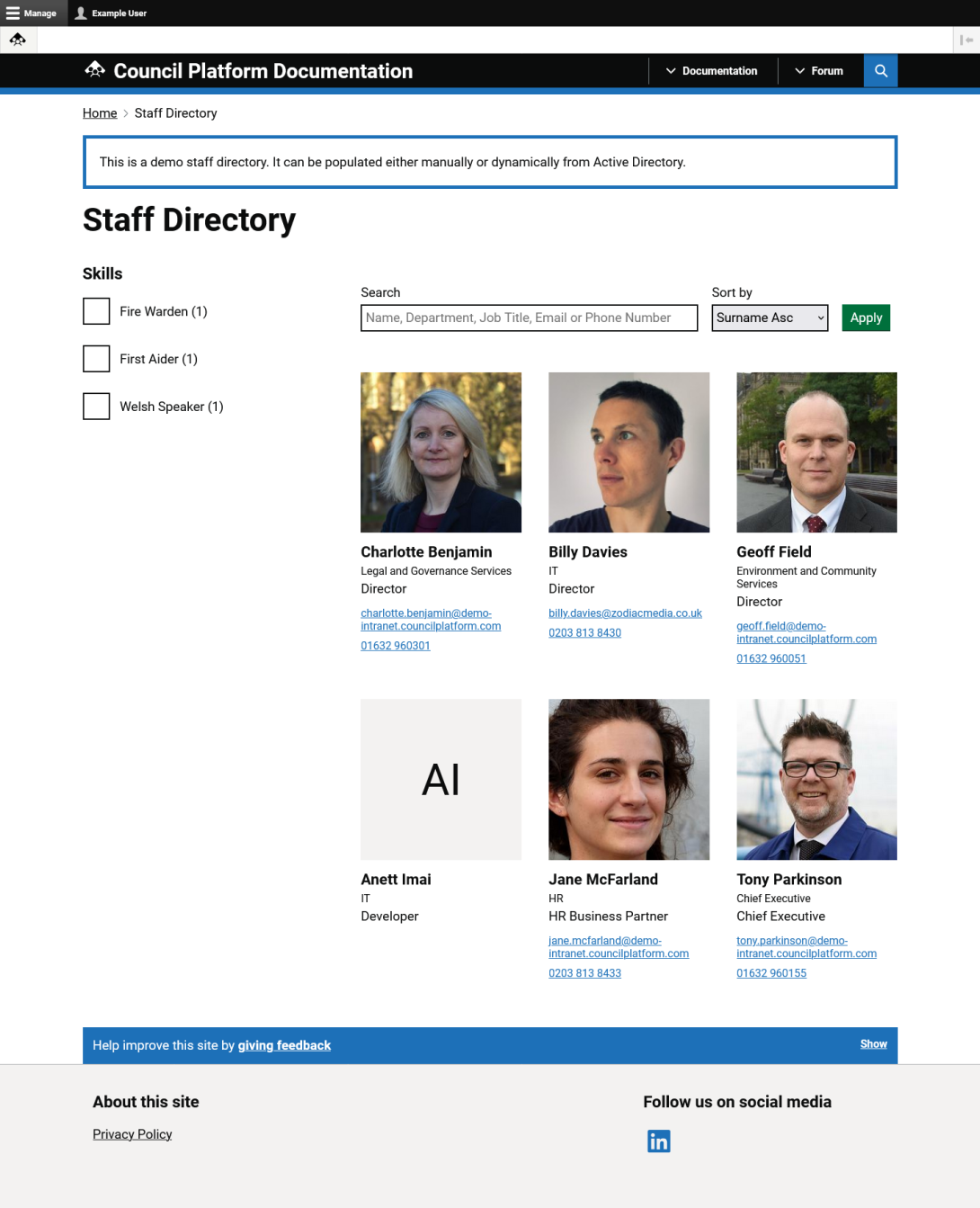
A simple demo staff directory.
Any data fields from Active Directory can be mapped through to user profiles.
Data changes in Active Directory are automatically synced, ensuring everything remains accurate.
As always, this improvement is free for all existing clients
These changes have been made in the core codebase of Public Platform, so will be freely available to existing subscribers as their sites are updated when we roll out the next security release of the product.